The hidden gem in Bitwarden’s Secret manager - bws run
Password and secret managers are ubiquitous these days and I feel like every one uses them these days (right? right?). Which is good, because they help us keep our secrets safe and secure.
I’ve been using Bitwarden Password manager personally for a couple of years now and I’ve been loving it. It’s open source , has a great community and has many features that I love (even in the free plan).
Recently, I’ve started to experiment with their Secrets manager CLI
-
bws - and one feature that struck me was the bws run command.
bws run
In a nutshell, bws run
allows you to run a command with secrests injected as environment variables.
That’s pretty neat.
What’s even cooler is that you can scope the secrets to a project and run commands with that project’s secrets. Let me show you how it works.
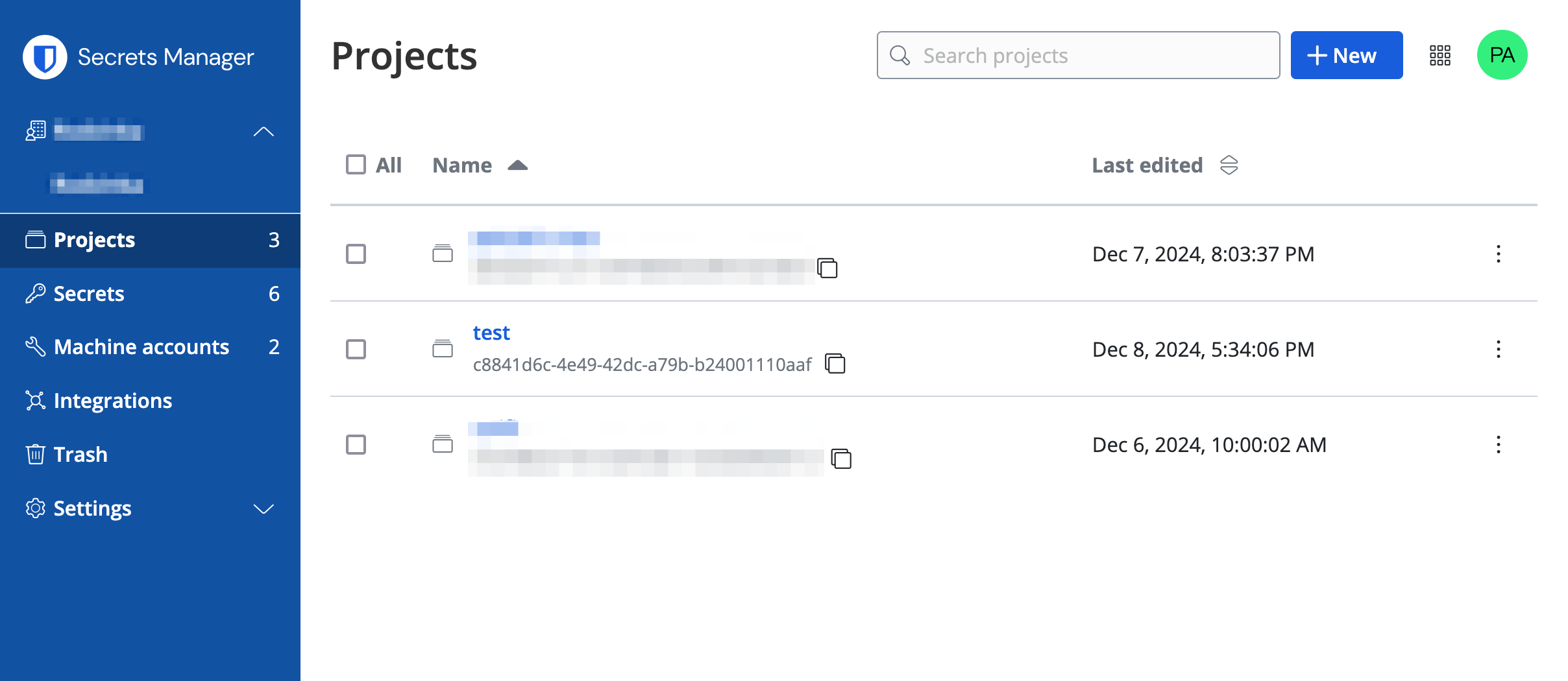
Project
First, you’d need to create a project in Bitwarden’s Secrets manager.
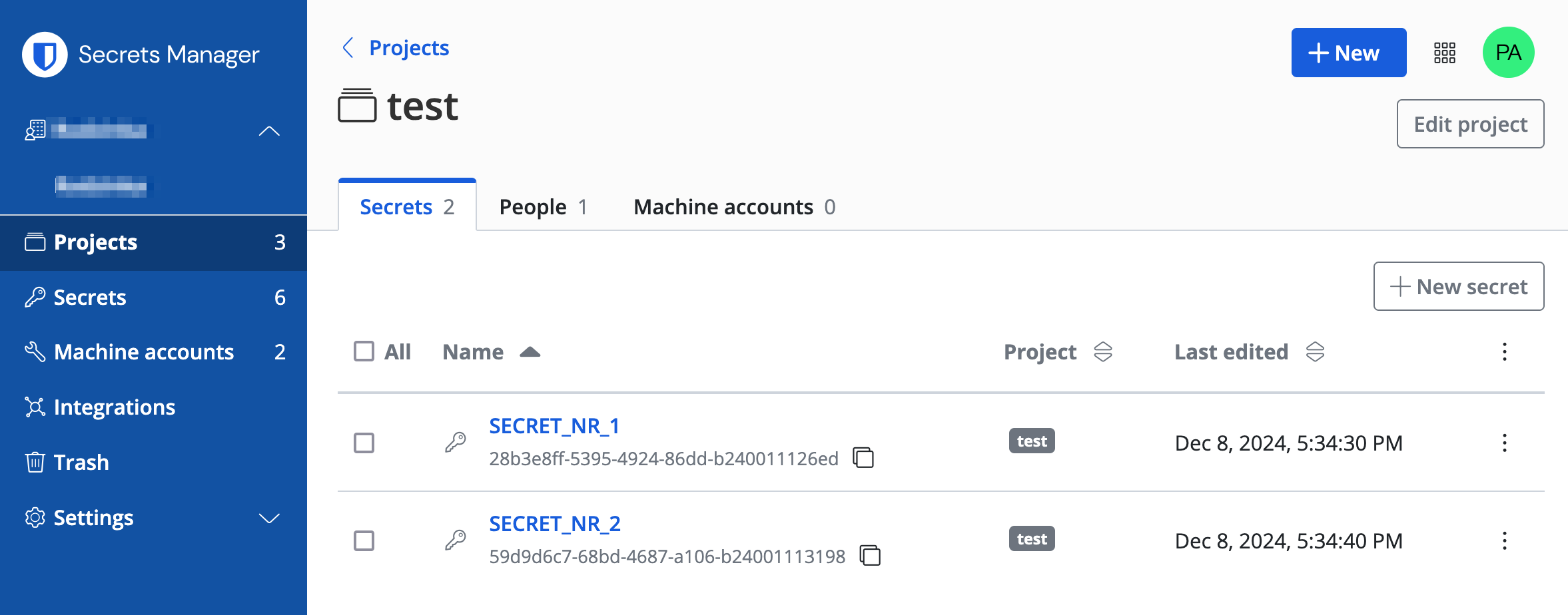
Secrets
When you have the project in place, populate it with secrets.
Machine account
In order to be able to use bws commands, you’ll need to create a machine account.
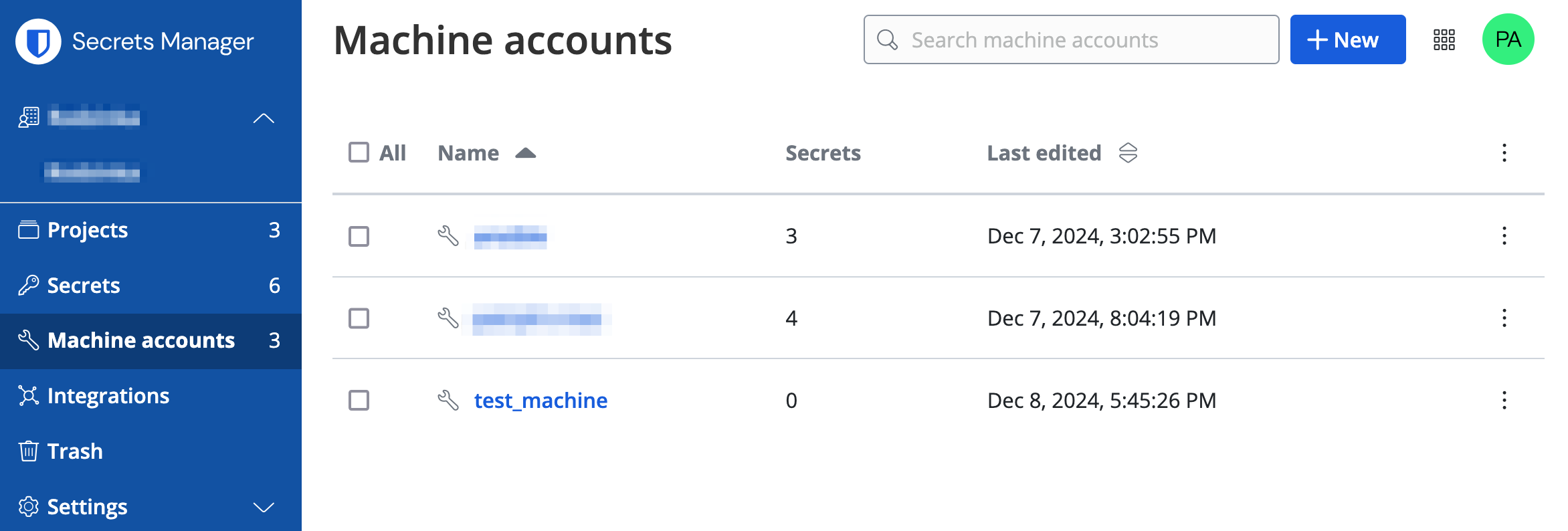
Machine account can be added to multiple projects so that it has access to their secrets.
I’ll only add read access to the test project but feel free to add more.
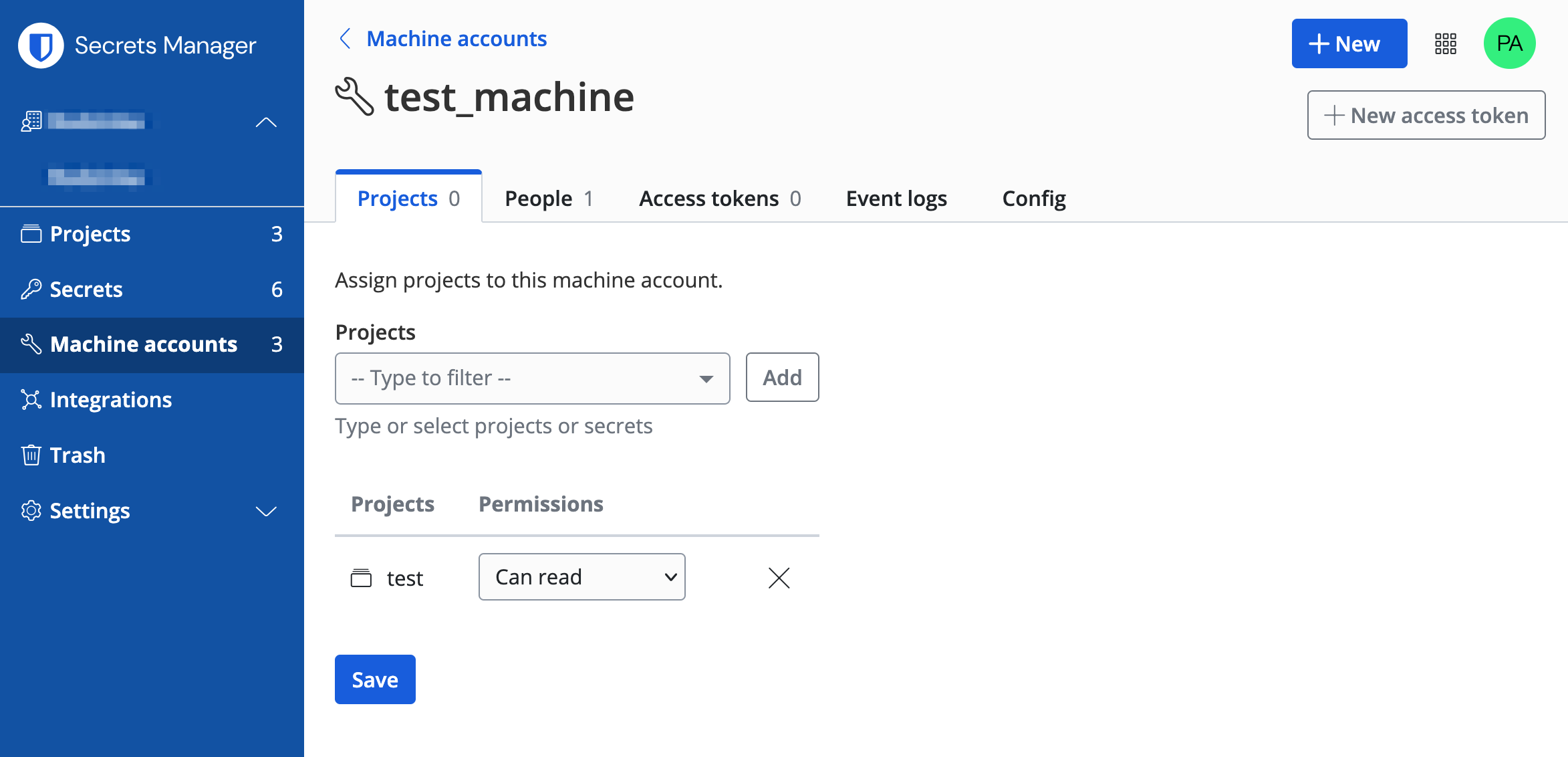
With that in place we can create the token for our machine account. Be sure to save it somewhere safe as it won’t be shown again.
bws will automatically use the token saved in BWS_ACCOUNT_TOKEN environment variable so you may want to use that for convenience.
Running commands
With all that in place we can run our commands and have access to secrets exported as environment variables.
| |
You can also constrain the secrets to a particular project by using the --project-id
flag.
| |
To limit the amount of variables provided to the command, we can also use --no-inherit-env
flag.
which will prevent the command from inheriting the environment variables from the current shell.